 |
| What is VPN How VPN Works? |
What is VPN How VPN Works?
Because we live in a connected world, security and privacy are essential to ensure ourpersonal safety from malicious hacks. from online banking to everyday contact with colleagues. We now regularly move data on our computers and smartphones, Finding ways to protect our digital life is extremely important, and for that reason VPNs (Virtual Private Networks) have become increasingly popular. VPN hides your IP Address to the Internet Server.
What Is VPN?
The VPN term stands for Virtual Private Network. As the name suggests, it provides users with a private virtual network so that they can connect to the internet in a way that is safe and stable. It preserves your privacy by allowing you to appear anonymously anywhere you want. Essentially, the main purpose of a VPN (Virtual Private Network) is to keep your private information secure.
A VPN (Virtual Private Network) is useful because it provides the connected devices with an acceptable degree of protection and privacy. This is particularly useful while the current network infrastructure can not be sustained on its own.
When the device is connected to a VPN (Virtual Private Network), the Device behaves as though it is on the same network as the VPN (Virtual Private Network). Each of your online traffic is transferred through a secure link to the VPN (Virtual Private Network). The System would then function as if it were on that network, allowing you to safely access local network resources. Irrespective of your position, you will be granted permission to use the internet as if you were present at the VPN (Virtual Private Network) site. This can be particularly useful for people using a public Wi-Fi network or a mobile Wi-Fi hotspot.
Then your device can contact the website via an encrypted VPN (Virtual Private Network) service link when you browse the Internet while on a VPN (Virtual Private Network). The VPN (Virtual Private Network) will then forward the request to you and forward the response back to the website via a secure connection.
How the Internet works, How big is the Internet: click here...
Types of VPN:
VPN (Virtual Private Network)s are very easy to use and are known to be highly efficient devices. They can be used to do a wide variety of things. Remote access VPN (Virtual Private Network)s, site-to-site VPN (Virtual Private Network)s and Mobile VPN (Virtual Private Network) are the most common types of VPN (Virtual Private Network)s
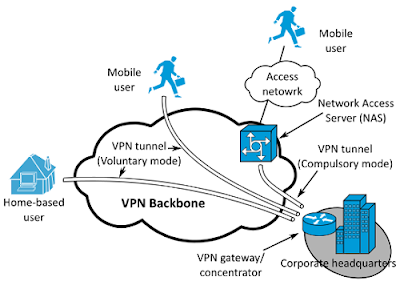
Remote access VPN (Virtual Private Network):
A remote VPN (Virtual Private Network) provides safe access to the network through public infrastructure like the internet. For organizations and their business networks, this is especially relevant.
This is important When workers connect to a public hotspot and use the Internet for work-related communications.
A VPN (Virtual Private Network) client connects to a VPN (Virtual Private Network) gateway on the company's network on the user's computer or mobile or tablet device. Usually, this gateway would allow the system to authenticate its identity. It will then build a network connection back to the system that allows it to access internal network resources such as file servers, printers, and intranets, as if it were on the same local network.
It normally depends on either Internet Protocol Protection or Protected Sockets Layer to protect your connection. SSL VPN (Virtual Private Network)s can also be used instead of an entire internal network to provide safe access to a single program. Some VPN (Virtual Private Network)s also have Layer 2 access to the target network, which would require a tunneling protocol such as the Point-to-Point Tunneling Protocol or the Layer 2 Tunneling Protocol running over the IPsec base link.
What Is IP address what happens if someone steals your IP address: click here...
Site-to-site VPN (Virtual Private Network):
That is when the VPN (Virtual Private Network) uses a gateway to connect to the whole network from one location to another. Many VPN (Virtual Private Network)s connecting via Internet use IPsec from a site to site. Instead of using the public internet, the primary transport of site-to-site VPN (Virtual Private Network) is typically using career multi protocol mark shifting clouds.
VPN (Virtual Private Network)s are also classified between conspicuous computers and they are often servers in multiple separate data centers. However, modern hybrid access situations have now replaced the VPN (Virtual Private Network) gateway in the cloud, usually with a secure link from the cloud service provider to the internal network.
Mobile VPN (Virtual Private Network):
A typical VPN (Virtual Private Network) may have an effect on the user experience when applied to wireless networks. It is safer to use a mobile VPN (Virtual Private Network) to get high speed and prevent data loss. Mobile VPN (Virtual Private Network) provides a high degree of protection for the difficulties of wireless communication. Mobile devices can have safe access to network services and software applications on their wireless networks. It's useful to use when dealing when you facing network problems, internet roaming, latency problems or low battery life, memory, or processing capacity.
Mobile VPN (Virtual Private Network)s are designed for a seamless user experience when devices switch networks or move outside of the coverage. It usually has a smaller memory footprint and thus, therefore, needs less computing power than the conventional VPN (Virtual Private Network). This allows the applications to run faster because the battery pack can last longer.
A Mobile VPN (Virtual Private Network) is a useful tool since it enhances privacy, user satisfaction, and productivity and also reduces unforeseen wireless support problems. The increased use and connectivity of mobile devices make sure you transfer your data through a safe network that is very important. It will give permission you to access the internet, while keeping your privileged information securely behind firewalls.
How your data Encrypted when you using a VPN (Virtual Private Network)?
Encryption is the term used to explain how the data is kept secret when you use a VPN (Virtual Private Network) Network.
Encryption protects information in such a way (basically converting it to gibberish) that it can not be read without a very strong password known as a key. indeed, this key breaks the complicated code that your data has been translated into. That data have in binary forms so that is converted into actual form. This key is accessible only to your device and the VPN (Virtual Private Network) server. The method of decoding the data is known as decryption, which is the method of re-reading encrypted information with the use of the word.
As a regular example, when you enter your credit card details on a shopping website, the information is encrypted and made unreadable before it reaches its final destination.
Various VPN (Virtual Private Network) providers use various types of encryption methods, but in a simple way, the VPN (Virtual Private Network) encryption process is like this:
When you connect to a VPN (Virtual Private Network), it's via a safe tunnel where your data is encoded. That means your data is converted into an unreadable codes like binary codes as it moves between your device and the VPN (Virtual Private Network) server.
Your computer is now perceived as being on the same local network as your VPN (Virtual Private Network). Therefore your Internet Protocol address (IP Address) would simply be the IP address of one of the servers of your VPN (Virtual Private Network) provider.
You can search the internet as you want, in the fact that the VPN (Virtual Private Network) serves as a barrier to protecting your personal information.
How effectively your data is encrypted depends on your VPN (Virtual Private Network) provider's encryption system protocols.
Who wants a VPN (Virtual Private Network)?
Users who access the Internet from a computer, laptop, or smartphone will benefit from the use of a VPN (Virtual Private Network). A VPN (Virtual Private Network) service will also improve your protection by encrypting and anonymizing all your online activities. Information transfer between your VPN (Virtual Private Network) server and computer or Smartphone are encrypted, so any web spying or hackers not able to trace your activity, what you are doing on any websites or web pages. They're also not be able to see private information including passwords, usernames, bank or shopping data, and so on. Anyone who wants to protect their privacy and online protection must use a VPN (Virtual Private Network).
What does the VPN (Virtual Private Network)?
The VPN (Virtual Private Network)'s fundamental principles are generally well known by most people. We believe the privacy of the internet is more than nice – it is important to the online world's success. That said, many people postpone obtaining a VPN (Virtual Private Network) because it is inconvenient or, worse still, unnecessary. They need not. They ought not to.
A clear way to demonstrate the need for a VPN (Virtual Private Network) is how unprotected you are when your Internet connection is not encrypted.
Basic Reason peoples Uses of VPN (Virtual Private Network):
People use VPN (Virtual Private Network)s for a number of different reasons. Some of these reasons are specific, while some people only have a VPN (Virtual Private Network) as another layer of security in contrast to a good anti-malware and practicing usually a sensible use of the Internet.
A popular justification for using a VPN (Virtual Private Network) is to keep anyone – from the Internet Service Providers (ISP) to public Wi-Fi hotspots – from monitoring what you're doing online. And Secure yourself from snooping on insecure Wi-Fi hotspots.
A lot like using a VPN (Virtual Private Network) is to gain access to regionally limited content, whether it's a TV show on your country's Netflix, or to get around some jurisdiction's internet surveillance rules. And bypass regional limits on sites or on streaming music and video.
At least achieve some anonymity online by covering your actual position.
Secure yourself from being logged in while torrenting.
Disadvantages Of using VPN (Virtual Private Network):
Just as there are several benefits of using VPN (Virtual Private Network) Private Network, there are also some drawbacks of using VPN (Virtual Private Network) in such a way that if you don't know about the disadvantages of VPN (Virtual Private Network), some of your personal and essential accounts can also be blocked.
If you open a Facebook account using a VPN (Virtual Private Network) network, your Facebook account will be blocked. You should never log in to a Facebook account on a VPN (Virtual Private Network) network.
Sometimes Google also banned your account for using VPN (Virtual Private Network) services.
One major problem is when you using free VPN (Virtual Private Network) services their giving so much adds to your browser
Also, decrease the speed of your Internet
Conclusion:
In this post, I explain VPN (Virtual Private Network) in a very simple way, like what is a VPN (Virtual Private Network)? What is the use of a VPN (Virtual Private Network) and how it works? You can use this to secure your data and, if you like, you can access those sites who banned in your territory area. Today, every company or organization is using its data to avoid thieves. Hope you have the right details here and if you liked this post, don't forget to share it, if you have any ideas or questions about this article, then make a comment.








0 Comments
Thank You, Give Your Review and Suggestion here.